
Securing Personal Data and Preparing for a Breach

What is CSR Readiness Pro?
The Readiness Pro comprises the patent-pending risk assessment program CSR Readiness and the award winning CSR Breach Reporting Service™.
How does the CSR Readiness Program work?
CSR Readiness Program is an on-line self-assessment tool that helps you review, revise and revisit your business processes for handling the personally identifiable information (PII) of your customers, employees and vendors, as required by a host of legislation and regulations.

Review – Take a Self-Assessment Evaluation
Detect all locations of personally identifiable information (PII) in an organization
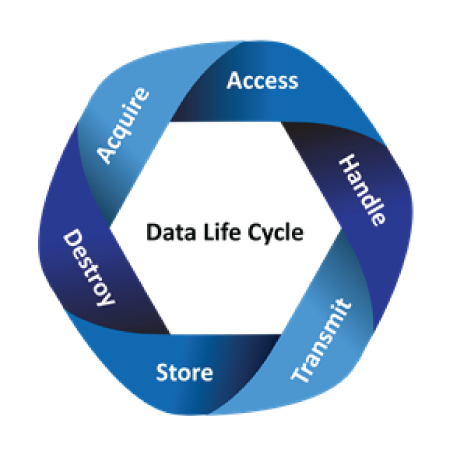
Determine how PII is:
- Acquired
- Accessed
- Handled
- Transmitted
- Stored
- Destroyed

Revise – Implement Readiness Policies and Remediation Instructions
Re-mediate weaknesses and train employees following system-generated policies and procedures

Revisit – Continually Improve Risk Score
Routinely monitor and audit performance to meet legal, regulatory and other compliance requirements
A dashboard will show progress and generate tasks to improve compliance. You can improve your business risk scores by remediation and implementation of further program offerings. Upon successful completion of the analysis and remediation, your business will earn a Certificate of Completion and the ID Stay Safe Digital Seal that you can use on your website and advertising.
What does the Certificate of Completion signify?
Once you have completed the self-assessment evaluation and implemented the remediation tasks, you will be awarded the Certificate of Completion. This can be placed on your website and is valid for one year from date of issue. By annually revisiting your self-assessment, you can maintain this Certificate of Completion.
What does CSR Breach Reporting Service do for me?
In the event of the actual or suspected breach of PII, the CSR Breach Reporting Service reports to authorities and notifies consumers, as required.
Your call to the in-house CSR team of privacy professionals initiates a custom evaluation of your incident to determine if authorities and consumers must be notified. CSR files the necessary breach reports on your behalf, and consumer notification can be prepared with your input.
Why do businesses need this Pro?
Many state, federal and international laws require businesses to protect the personally identifiable information (PII) of employees, vendors and customers. Penalties for noncompliance can include fines, prosecution and even jail time. Massachusetts and Connecticut are just two examples of many jurisdictions that require businesses that deal with their residents to maintain comprehensive risk assessment, remediation and monitoring programs related to their handling of legally protected PII.
If organizations don’t have this program, what could happen?
While it’s impossible to completely avoid a breach due to uncontrollable circumstances, 97% of breaches could have been prevented. Accidents, errors and theft are just a few ways that information is compromised. Smart devices and wireless services compound the problem. Proactive detection and correction can go a long way to prevent loss and further fallout due to reputation damage, lost sales, fines, lawsuits and prosecution.
The Department of Homeland Security, the FTC, Visa and the BBB encourage businesses to protect consumer data and plan ahead to reduce risk. All states have laws that protect their residents who might be your customers, employees or vendors. Many laws specifically require creation and maintenance of information security programs. These laws include penalties for noncompliance.
For example, the civil penalty for violating the Connecticut Act No. 08-167, which requires the safeguarding of personal data, is $500 per violation, up to $500,000 for a single event.
Lost trust means lost sales. The fallout of data breaches has caused businesses to close their doors. According to Visa, businesses should “consider a breach likely and plan accordingly.”
Does Breach Reporting Service only cover items stored with IDSAutoshred?
No, the Breach Reporting Service covers the location contracted with IDSAutoshred and handles reporting and notification as needed for the breach of all PII data your business may have, whether it is stored in your office, in file an employee takes home, or on a business laptop that is stolen while you are away on vacation.
Definitions
What is personally identifiable information or PII?
The simple answer is that it’s anything that can be used to identify you. The loss of this information leads to identity theft.
Types of personal information include: name, address, phone, email, birth date, Social Security number, driver’s license, bank account and credit card information. The list continues to grow with new and revised legislation and court rulings.
Other personal information includes health information, medical records, vehicle identification numbers, license plate numbers, login credentials and passwords, school records, and even voice recognition files. Fingerprints, retina scans, and hand prints are also considered personal information.
What is the difference between PCI and PII?
PCI data is just one type of personally identifiable information. The PCI Data Security Standard protects credit card holder data such as debit or credit card number, expiration date and card security code.
What is a breach of PII?
The unauthorized access, loss, use or disclosure of information by either accident or criminal intent which can identify an individual is a breach of PII.
What is data breach reporting?
When a breach occurs, the clock starts ticking to comply with federal, state and other laws. Reporting involves the where, when and how of the incident.
What is consumer notification?
Almost every state has enacted a data breach notification statute. These laws generally require businesses that have personal information about residents within a state to notify those residents when that data is compromised.
Is this insurance?
No. The CSR Breach Reporting Service reports to authorities and notifies consumers, as required In the event of the actual or suspected breach of PII, and this can reduce your liability; but the service is not insurance to cover loss or legal costs.
What are some examples of a breach?
A breach can occur in many ways, including through lost laptops or smart phones, loss or improper disposal of paper records, intrusion into your network or PC by hackers, and theft. The definition continues to expand.
Requirements to Protect Data
Who do I need to report a breach to?
Who you need to report to in the event of a particular breach depends on many factors, including where you are located, what kind of PII was involved in the breach, and the location of the individuals whose PII may have been compromised. Over 100 countries have data protection laws, as well as 300+ federal, state, provincial and local authorities in the U.S. and Canada.
Does CSR determine whether a breach occurred?
No. Based upon our interview with you, our Privacy Professionals determine whether reporting to authorities or notification to consumers is necessary. If reporting is required, our Privacy Professionals will do so on your behalf. If consumer notification is necessary, we will work with you to do so.
What laws govern PII?
Here are a few examples of the hundreds of laws and regulations that relate to the protection of personally identifiable information (PII) and requirements to report suspected or real loss.
- Gramm-Leach-Bliley Act (GLBA)
- Fair Credit Reporting Act (FCRA)
- Drivers Privacy Protection Act (DPPA)
- Health Insurance Portability and Accountability Act (HIPAA)
- Health Information Technology for Economic Clinical Health (HITECH) Act
- Payment Card Industry Data Security Standard (PCI-DSS)
- Family Educational Rights and Privacy Act (FERPA)
- 50 state data breach laws
- Data security laws requiring comprehensive information security programs to safeguard personal information, i.e. Massachusetts’ 201 CMR 17.00
Who are the enforcement agencies and others who might be involved after a breach?
Enforcement officials include various federal and state agencies as well as attorneys general, commissioners and others. Here are a few examples:
- Federal Trade Commission (FTC)
- Consumer Financial Protection Bureau (CFPB)
- Card brands like Visa and MasterCard
- State Attorneys General
- Federal Bureau of Investigation (FBI)
- US Secret Service
- Dept. of Health and Human Services/Office of Civil Rights
What if PII shared and/or received from another organization is compromised?
If your business is a third-party provider with PII of customers, employees, or vendors of another business, then, depending upon circumstances, you very likely are required to protect a breach of that data.
What if PII under my care is encrypted, redacted, or masked?
Even if the material is encrypted, redacted or masked, various regulations still require its protection. For example, encryption keys must be secured.
How can I limit the threat of a data breach?
Almost everyone can do more to protect PII. CSR Readiness helps you assess your risk in handling PII, re-mediate your processes, implement policies, train staff and continue to monitor and audit, as required by laws and regulations.
About CSR
Who is CSR?
CSR Privacy Solutions, Inc. is a leading provider of award-winning data life cycle management and expert services, including the patented, award-winning CSR Breach Reporting Service™, for businesses domestically and around the globe.
CSR enables compliance with PII requirements, while facilitating best practices to reduce business risk and financial liability associated with the acquisition, handling, storage, sharing and disposal of data.
How many companies use this service?
Hundreds of thousands of businesses have enrolled in CSR data management and breach services.
Can you help me with other privacy services?
Other services include PII business analysis, remediation, audit, forensic, education, certification, special projects and Stand-In Privacy Officer provision.
In the News – Privacy Breach Fines
| Location | Industry | Company | Year | $ Amt Fined | Assessed Fine | Link – Article |
|---|---|---|---|---|---|---|
| New Jersey | Healthcare | Virtual Medical Group | 2018 | $416,816 | NJ AG | Order |
| CA | Tech | Unixis, Inc | 2018 | $98,618 | NJ AG | Article |
| Iowa | Tech / Retail | DealerBuilt | 2018 | $80,784 | NJ AG | Blog Post |
| Georgia | Tech | Best Medical Transcription | 2018 | $200,000 | NJ AG | Article |
| New Jersey | Healthcare | EmblemHealth | 2018 | $100,000 | NJ AG | Article |
Learn how we can help you save money with our effective document shredding plans.
Call: (877) 886-4732
We Value Our Customers!
We’re here to help your business and personal assets through efficient processes, mobile technology, & great customer service. We offer 10% discount in your initial shred.
Our goal is to provide excellent customer satisfaction using high technology and good old fashion customer care.
Peter Levitt, CEO, IDSAutoshred


